
What have you heard about the vulnerability called Heartbleed? More than you wanted to? Less than you needed to? Let me unpack it for you, only the part that you need to know, and then I’ll get a little deeper for those who want to stick around for the full meal. Let’s do a Good News/Bad News thing.
What you need to know is that some websites, but not all of them, were susceptible to a certain type of attack that can steal your passwords. Here’s the good news: Your bank is probably not one of them. Here’s more good news: most website owners who were susceptible have already fixed the problem and sent out notification that you should change your password. If you got one, DO NOT IGNORE IT. Here’s some bad news: Not all the ones still vulnerable are sites you would be okay with having your stuff compromised. More bad news: You may not have heard from them yet because they may not have fixed the problem yet.
The good news: This is a recently-discovered vulnerability and has not been widely exploited, but if the one whose stuff got stolen is you, it really wouldn’t matter how widely it was exploited, would it? This article on Wikipedia indicates that there have been just a handful of thefts resulting from it. (More good news, right?)
A little more bad news: Remember my post about how you could tell if a website was using security? With this bug, none of that makes any difference. Well, that’s not exactly accurate. For a compromised website, it doesn’t matter if it is using Secure Sockets Layer (SSL), because that’s the part that got compromised.
Aaaaand the good news….within a few days–which, seriously, is amazingly fast–of discovery of this vulnerability, the patch for the vulnerability was issued.
Now what to do about it: First, as I said, if you got a notice to change your password for a website, do it. Immediately.
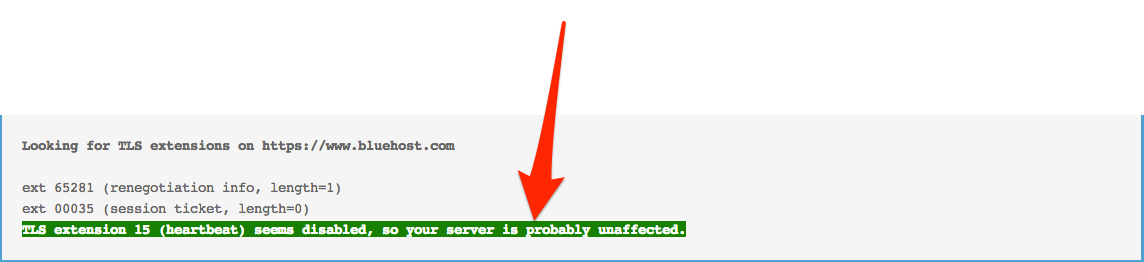
If you have not gotten a notice from one of the sites where you transact business, for example, a bank, or a store you’ve done business with, or from one of the sites where you may store personal information such as Facebook, and you would like to know if that site is vulnerable, you can use this site to test that portion of the site’s security. When you get there, type in the website address of the site you want to test. And this is what you hope to see:
![]()
![]()
![]()
![]()
The vulnerability was discovered by two groups independently, and the cool thing is that neither one is claiming exclusive credit. Google’s security team was the first to report it, but it was also discovered by a cybersecurity firm in Finland called Codenomicon. The name of the bug is derived from the name of the process it messes with. SSL uses a Heartbeat Extension to test secure communication links. The vulnerable implementations were using OpenSSL, but OpenSSL is not by any means the only provider of SSL, and not all implementations of OpenSSL are vulnerable. This particular problem was a New Year’s Eve release. The actual error in the code was quite small; but obviously it had a huge impact. OpenSSL is an open-source project, which means that the code is freely available to review, change, and release. This is good, and this is bad. It’s good because it can call into service the best coding minds in the world to create, improve, and fix codes. It’s bad because the bad guys can look at the code and see where it’s weak, which is what evidently happened. But because the code was available to review, the Google team was able to create a fix for code they didn’t author, and the patch has been made available for application under what should be the same freely available license that the original code uses. It now passes to website owners to apply that patch to their servers.
Now–about that password change requirement: Go to that website where you can test the SSL implementation of the sites you have interest in, test the site, and if it passes with the result shown above, go ahead and change your password. If you find a site with a vulnerability, alert the webmaster using the contact information available somewhere on the site. It won’t do you any good to change your password until they fix it, because the Heartbeat Extension is still vulnerable and can still toss your password out for the asking, and there’s nothing you can do about it. Pay attention, keep checking until it shows up as “unaffected” at that test site, and then change it. And if there are any vulnerable sites where you have used a debit or credit card or bank account information, you will need to keep a very close eye on those accounts for at least three months. Any suspicious activity should show up by then. No guarantees, but when financial information gets sold on the black market, the buyers want to use it pretty quickly before it gets shut down by the issuing institution.
This is a simplified explanation of the issue, so what did I leave out? What else would you like to know about Heartbleed?
![]()