PHISHING is an attempt to get you to give up some of your login credentials. Most commonly, these attempts will come to your email inbox, and some of them are quite convincing. Recently I received one that my email account correctly identified as spam, but it was so well crafted that I thought it provided excellent material to show you how to tell the difference between a real site and a phishing attempt.
First let’s look at the email itself:
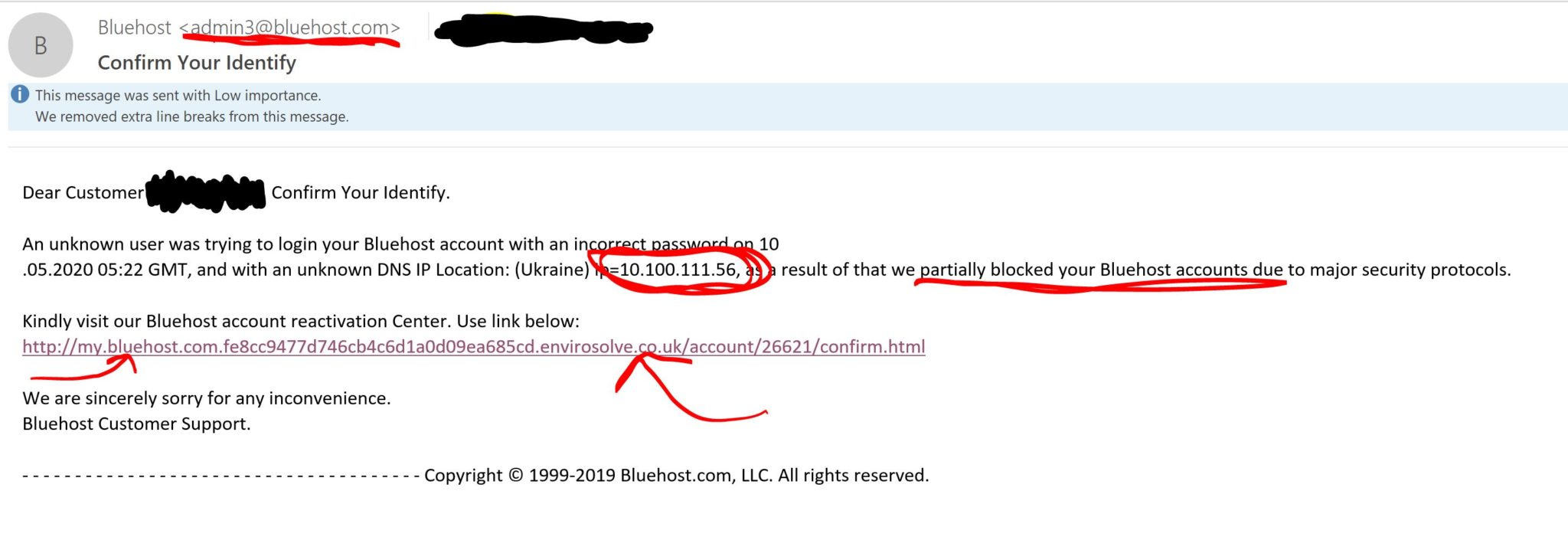
The sender’s email address is different from the address that usually sends communication to me. The numerical address I circled caught my attention because addresses that begin with 10 are private addresses, used only internally to an organization. They’re also not routable, which means that an email originating from that numerical address could never land in my inbox because a router would never pass it on from the internal organization to a different network. The only way for me to receive an email from an address beginning with 10 is if I am using addresses beginning with 10 in my own network and the email came from somewhere in my own network. Bluehost is not in my own network.
The link in the address does not indicate Bluehost itself, which is another red flag. The URL is my.bluehost.com, followed by a string of numbers, which is not where I would go to log in to my Bluehost account. The other underlined item shows a domain that indicates something other than Bluehost.
I used a virtual machine to follow the link, in case the site wanted to serve up malware. I also navigated to the real Bluehost site, the place I go when I actually want to do something there. I had no intention of actually logging in to the bogus site from the link in the email, for several reasons, and that, more likely than a malware infection, was the objective–to gain my login credentials.
Let’s look at the address bar of the bogus site:
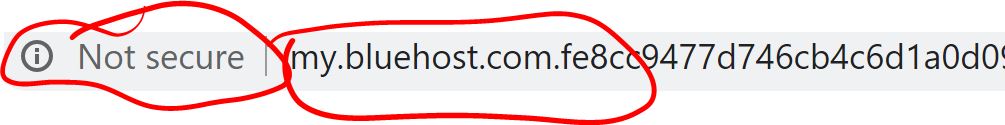
First, we see that Chrome has identified it as Not secure. This site is not using Transport Layer Security (TLS) to encrypt my logon credentials. This is not the sort of behavior I would expect from my web hosting company. Additionally, the string of numbers after the name is an IPv6 internet address, directing the browser to a login page that the phishers didn’t even bother to conventionally name.
Now let’s see the real Bluehost address bar:
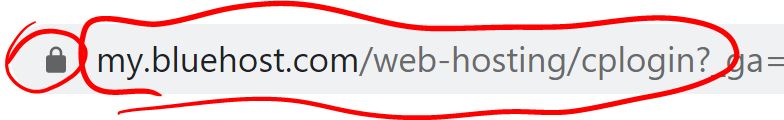
The first thing we see is the padlock. Bluehost uses TLS to encrypt my login credential transmission, so an attacker can’t read them during login. Bluehost directs my login to its control panel page, and this is what we see in the address bar.
One final indicator comes from my use of a product called LastPass, my password manager. I use the LastPass browser plugin and it will autofill certain fields for me, under certain conditions. One of those conditions is that LastPass must recognize the URL, the web addrses, of the page I’m trying to log into. Here’s what happens when I go to BlueHost by typing in the address:
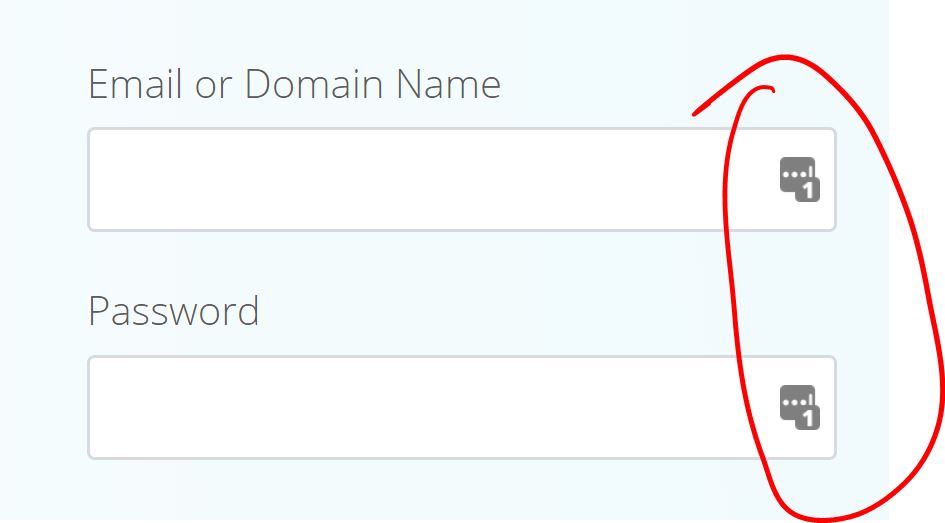
At the right end of the email and password field we see the LastPass icon. We also see an indicator that LastPass holds one set of login credentials for the page we’re on. LastPass has recognized that this is the page I was on when I set up the login password in LastPass. But look what happens when LastPass doesn’t recognize the page:
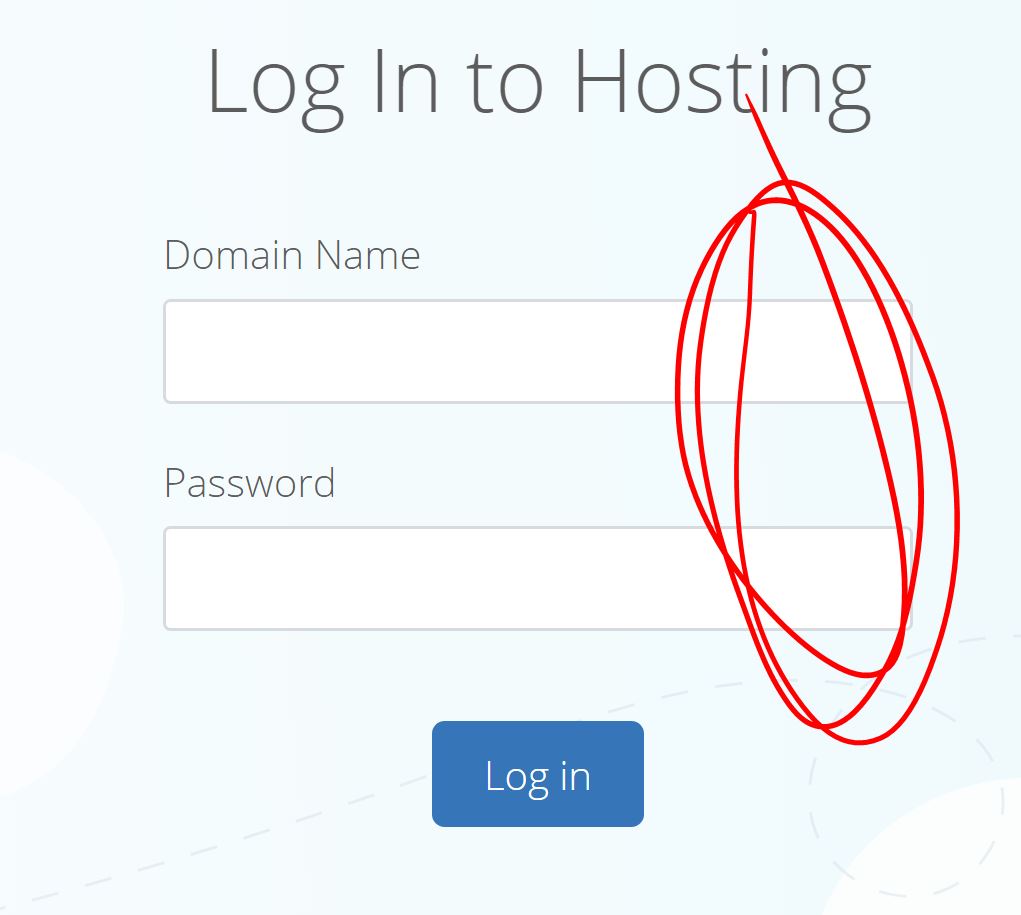
There is no indicator that LastPass knows this page. I could still copy and paste my login credentials into these fields, and there would be nothing to stop me from doing so. However, the absence of those little icons told me that LastPass didn’t see this page as something it knew.
LastPass would not have prevented me from entering my credentials here, but it provided a visual indication that something unexpected happened. This is a personal endorsement of LastPass, and LastPass does not pay me for it. I pay for a version of LastPass because it provides me with a lot of convenience and security that would be difficult and cumbersome to implement manually. But mainly, I wanted to show you a few of the things you can look for if you suspect an email is a phishing attempt.
- Know the sender’s address
- Look at the numerical IP address, and ask a geek of you don’t know what it means.
- Never use an email link to log into something important where you will have to supply credentials
- If in doubt, contact the organization directly and ask their advice. They will know if they have locked your account, and exactly why, and what to do about it.
I wrote about LastPass in a previous post, if you want to learn more about it.